IT Management
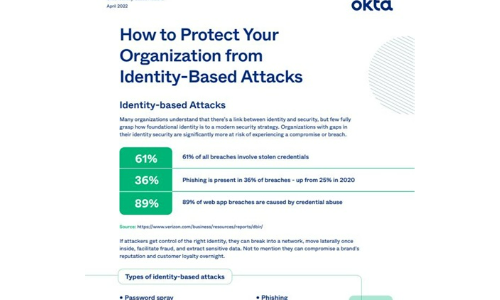
How to Protect Your Organisation from Identity-Based Attacks
Many organizations understand that there's a link between identity and security, but few fully grasp...

IAM for the Real World: Identity Governance
In the real world, governance is a major challenge. In fact, governance can't even be considered until...

Effective License Management With A Changing Remote Workforce
Peter Drucker, one of the most widely known and influential thinkers on management, is credited with...

High Speed Network Encryption
High Speed Encryption (HSE) secures data in transit and data in motion, as it moves across the network...
4 tips to ensure your board is ready for a successful AGM
The 2022 AGM season is on course to see unprecedented levels of challenge for boards and businesses....

Definitive Guide to SOAR
How to stop threats faster with security orchestration, automation, and response. Cybersecurity organizations...

Securing Microsoft 365
Few tools are as critical to modern business as Microsoft 365. Unfortunately, the platform's ubiquity...

4 Low-Code Best Practices for SAP Fiori Apps
It has been proven that enterprise IT teams that include a no-code/low-code approach for their SAP app...

E-signatures for Global Businesses
This eBook covers the benefits and challenges of electronic and digital signatures, compliance considerations,...

6 ways cloud computing can support your security capabilities
Embracing cloud computing forces organizations to decide between the cost-effectiveness, scalability,...

Building Your MSP Security Offerings
As a managed service provider (MSP), your customers already expect you to keep their networks secure....

Drive Infrastructure Optimization with Predictive Analytics
As cloud architects move more workloads to public and private clouds, hybrid multicloud architectures...

How Proofpoint EFD Is More Than Just DMARC
A raft of solutions have sprung up to help organisations set up and manage their DMARC strategies. Like...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.
