Internet of Things (IoT)
The 5G opportunity within UK industry
Neos Networks research shows that two thirds of organisations expect to have made significant investment...

Deploying Flexible Data Protection to Support Cloud Workload Placement
Digital transformation (DX) projects are designed to help organizations better utilize data for competitive...

The Future of Government Operations Depends on Digital Transformation
New technologies can help government organizations reduce costs, improve constituent services, and quickly...

Empowering Medical Manufacturers to Become Leaders
Due to increasing technology and product complexity, regulatory requirements and supply chain issues,...

5G Is Changing the Game - Right Now. Is Your Infrastructure Ready?
Advanced 5G use cases will require a fundamental change in infrastructure before they can scale. As network...

Connected cities and places
Improving digital infrastructure is key to enabling a smarter city or place to develop, thereby creating...

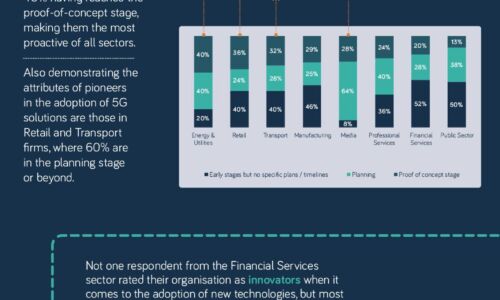
5G for the enterprise
With a desire to better understand the current, on-the-ground reality for enterprises and organisations...

Core connectivity as a key enabler for smart cities
With urbanisation continuing at breakneck speed around the world, governments need solutions to make...

Employees are choosing how they work
'The measure of intelligence is the ability to change.' To remain connected, productive and secure in...

Bloor Research Data Governance Market Update
Streaming analytics is a space that is largely built on the back of stream processing. In turn, stream...

Microsoft Digital Defense Report
Over the past year the world has borne witness to a burgeoning cybercrime economy and the rapid rise...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


