
The Forrester Wave™: Enterprise Email Security, Q2 2021
In a 25-criterion evaluation of enterprise email security providers, Forrester identified the 15 most...

Comparing AWS Tools for Cloud Cost Management and Optimisation
Cloud cost management and optimization can become a big challenge as organizations find that the decentralized...
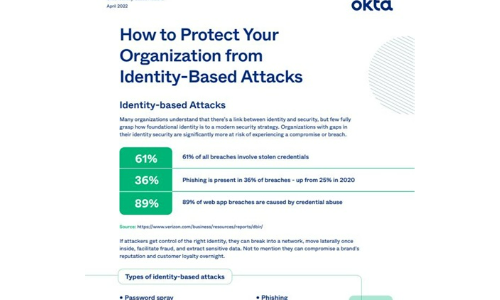
How to Protect Your Organisation from Identity-Based Attacks
Many organizations understand that there's a link between identity and security, but few fully grasp...

The CIO's Guide to Transformation with AppExchange
A huge part of a CIO's role is 'keeping the lights on'. They are responsible for making sure systems...

5 CRM Strategies for Effective Cross-Selling and Upselling
Effective cross- or upselling improves customer loyalty, deepens customer relationships and ultimately,...

2022 Annual State of Phishing Report
Enriched with robust threat intelligence from the Cofense Phishing Defense Center (PDC), which analyzes...

Your Path to Zero Trust
In a business world without perimeters and dominated by remote work, finding a balance between easy collaboration...

APIs For Dummies
APIs are a hot topic, energetically debated by businesspeople, IT managers, and developers alike. Most...

Third-party Risk Management Essentials
From big banks and university hospitals to retail fashion chains and every level of government, organizations...

Confronting the NEW WAVE OF CYBERATTACKS
Like the virus responsible for the worldwide pandemic, email-based cyber threats continued to mutate...

DEIB Analytics: A Guide to Why & How to Get Started
Gain insights from RedThread Research on why businesses are focused on diversity, equity, inclusion and...

Designing Hyper-Aware Healthcare Facilities
At its core, the Internet of Things (IoT) is an amalgamation of machines in the physical world, logical...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

