Software

Enabling the Modern Business Through IT
As the pace of innovation accelerates, customer needs change and industries converge, many companies...

8 Ways To Evaluate An MDR Provider
For many organizations, digital transformation had been a business initiative for years, but the pandemic...

Delivering Business Transformation for Fintech Companies
The financial sector has seen an influx of innovation and competition in recent years led by fintech...

5 Steps to Improving Knowledge Management
Advania is an official partner for 4Industry, the digital knowledge management platform for the manufacturing...

Reinventing customer service
The upheavals of 2020 created an opportunity for customer service teams to rethink service delivery and...

Rethinking Insider Risk in the Gig Economy
More and more companies are relying on gig, contract and freelance workers to scale their business. Fully...

An IT Strategy to Support the Modern Analytics-Driven Business
For IT organizations, the requirement for high-performance systems and analytics tools that work with...

How to Ensure Flexibility in a HMC Strategy
Enterprises are moving rapidly to diverse cloud models, including hybrid cloud, multicloud and connected...

4 steps to transforming employee journeys
Delivering a best-in-class employee experience is essential as remote work gains momentum. Read about...
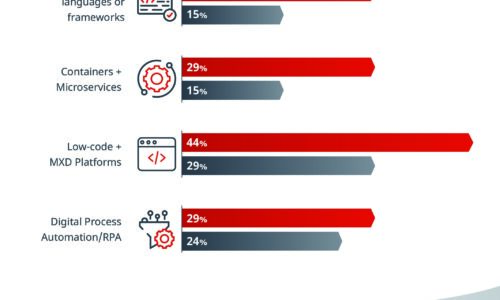
What Separates the Best from the Rest
Some IT organizations have the speed and adaptability to change course quickly when disaster strikes...

5 Principles For Securing DevOps
DevOps, a new model for software development, is transforming the way the world creates software. And...

The Complete Guide to Enterprise Ransomware Protection
The SentinelOne Complete Ransomware Guide will help you understand, plan for, respond to and protect...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

