Software

7 Ways to Work from Anywhere
Bring security and speed to the office of the future Following a massive global influx of remote work,...

Make your enterprise resilient with critical event management
Many enterprises are under-prepared or lack the technology to respond well to critical events like these: Read...

DEVSECOPS: Staying Secured and Compliant in a High Paced Release Cycle
The rapid adoption of cloud technology and evolution of the software industry from monolithic applications...

Modernize Endpoint Protection and Leave Your Legacy Challenges Behind
2020 was an unprecedented year for security teams amid the global health crisis. The threat landscape...

Inside Complex Ransomware Operations and the Ransomware Economy
Ransomware operators have steadily become more sophisticated and more aligned with nation-state actors,...

Mobilising employee productivity in the distributed workplace
Citrix and Microsoft shape modern workplaces that unite the essential elements of today's distributed...

Change management blueprint for contact centre digital transformation
The COVID-19 pandemic put organisational change into hyperdrive. Businesses were compelled to move to...

eBook: Product development strategies managed with cloud PLM
Discover how your product development strategies can benefit from modern cloud software-as-a-service...
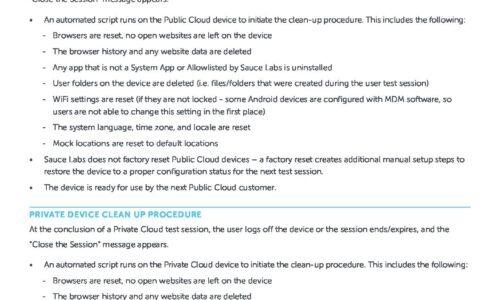
Public & Private Device Clean Up Procedure
This data sheet explains the options available when you want to make sure that your content, or some...

How to Secure Multicloud
The promise of cost savings, flexibility, and agility is making it easier for more organizations to embrace...

The Ultimate CX Agent Guide
Customers have embraced technology to manage all aspects of daily lives, setting off a digital disruption...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.