Private Networks

Securely Work From Anywhere With the Fortinet Security Fabric
The way people work has fundamentally evolved, and organizations need to be able to keep workers productive...

Your Path to Zero Trust
In a business world without perimeters and dominated by remote work, finding a balance between easy collaboration...

Global Threat Landscape Report
Another half-year through unprecedented times has passed. But as unique as these times may feel, we continue...

Tanium Insights: It's Time to Ditch the VPN for Zero Trust
Many organizations have started adopting zero trust strategies to protect their distributed networks...

The State of Zero Trust Report
The zero-trust network security model has become a pervasive topic for IT professionals. Many organizations...

How SASE empowers your business for the cloud generation.
Wide area networks (WANs) have played a critical role in business growth for several decades. Early WANs...

Zero Trust Access for Dummies
As businesses continue to embrace digital innovation, cloud applications, and the new work-from-anywhere...

5G for the enterprise
With a desire to better understand the current, on-the-ground reality for enterprises and organisations...

Hybrid Work Drives the Need for ZTNA 2.0
The COVID-19 pandemic has had a profound effect on the world. Businesses have compressed into months...

Getting Started with SASE
Secure Access Service Edge: A guide to secure and streamline your network infrastructure As enterprises...

Reinventing work
We're coming off one of the most challenging years in business history. The pandemic forced every company...

Trusted Access Report
As global conflicts spill into the digital realm, protecting people through to the enterprise is increasingly...
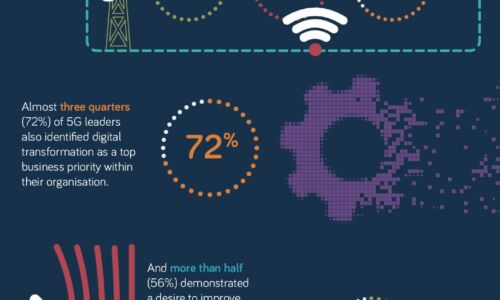
What makes a 5G Leader?
With 5G a still nascent technology, opportunity remains for businesses to accelerate adoption of this...
- 1
- 2
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.
