NAS

Bilfinger Protects Supply Chain Email Communications
Restores confidence in email and prevents brand misuse through authentication. Cyber criminals use fraudulent...

Practical Guide To A Zero Trust Implementation
Zero Trust is becoming the security model of choice for enterprises and governments alike. However, security...

Deliver a CMDB with true business value: 6 essential steps
Your Configuration Management Database (CMDB) provides accurate and reliable information about digital...

Dell EMC PowerStore: Oracle Database Best Practices
This paper delivers guidance for using Dell EMCTM PowerStoreTM T model arrays in an Oracle® 12cR2 (and...

Ransomware Protection with Pure and Veritas
Ransomware attacks continue to be top-of-mind for business and IT leaders. And for good reason. Ransomware...

Compliance in the Age of Digital Collaboration eBook
In today's business landscape, more people are working remotely. Far-flung teams work together across...

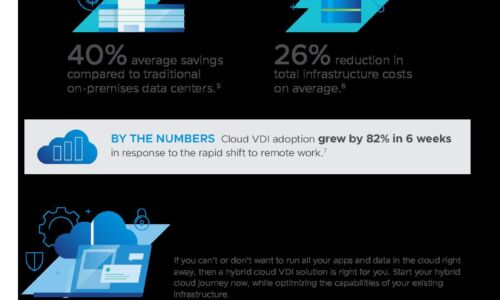
How Cloud Desktops Support Workforce Agility
How fast is the number of devices users employ growing? It has been more than four years since GSMA Intelligence...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.