Mobile Computing

Low-Code Guide
Low-Code development is the way to build apps more quickly by reducing the need to code. But that's not...

Why dirty data can stop quote-to-cash processes in their tracks
It's been 15 years since mathematician Clive Humby uttered those famous words: 'Data is the new oil....

GigaOm Radar for Phishing Prevention and Detection
Get your complimentary copy of this independent GigaOm Research report, which analyzes positioning and...

Verizon and Palo Alto Networks Enabling a Secure Connected World
Supporting mobility, minimizing the attack surface, and having reliable access to applications are key...

5 Critical Requirements for Internal Firewalling in the Data Center
Preventing hackers from hiding inside large volumes of east-west network traffic has now become critical...
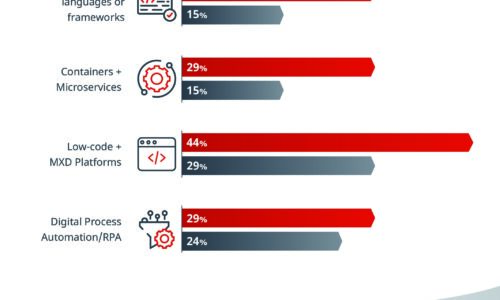
What Separates the Best from the Rest
Some IT organizations have the speed and adaptability to change course quickly when disaster strikes...

Windows Cost Savings Infographic
Save by moving Windows workloads to AWS Companies can lower infrastructure costs while improving performance,...

The data challenges in usage-based subscriptions
The boldest companies are taking note and giving their customers the usage-based pricing they want. And...

The Zero Trust Guide To Remote Worker Security
With the recent increase in the number of employees working from home as a result of the COVID-19 outbreak,...

Embark on a Mission to Hybrid Cloud
Today's businesses need to move and grow quickly—supported by flexibility and reliability. When you're...

Refresh your thinking: You've got a platform problem
The pressure on IT is mounting. Can you meet it before it becomes too great for today's systems and processes?...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


