IT Threats & Vulnerabilities

Centralised Control Simplifies Management, Boosts Security
Aquila Heywood wanted to update its privileged access management processes to increase data security...

The 3-2-1 Data Protection Rule and Hybrid Cloud Backup with NetApp
IT teams are under extreme pressure to improve backup, disaster recovery and data protection to eliminate...

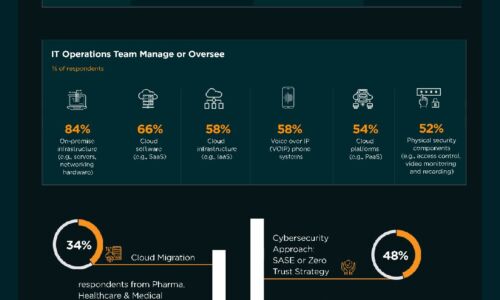
How to Create a Successful Cybersecurity Plan
Along the edge of subway tracks in the UK is a sign that says, 'Mind the gap,' warning passengers to...

You've Got BEC!
A Roundup of the 10 Biggest, Boldest, and Most Brazen Business Email Compromise Scams of 2020 and 2019. It's...

Use Case-Driven Cloud Security Evaluator Guide
Researching cloud security? Be sure you evaluate yourself and your vendors on the 6 most common cloud...

Encryption, Privacy, and Data Protection: A Balancing Act
The Business, Privacy, and Security Mandates for Comprehensive SSL/TLS Inspection. Enterprise IT leaders...

7 Experts on Moving to a Cloud-based Endpoint Security Platform
Without a doubt, endpoint security has become an urgent priority for many organizations, and it's not...

Enhanced Privilege Access Management Solutions
Privileged Access Management (PAM) is one of the most important areas of risk management and security...

Securely Enabling a Hybrid Cloud in Microsoft Azure
The public cloud has rapidly moved past the novelty, curiosity stage to the business critical initiative...

Deploying Consistent Application Services in Multi-Cloud Environments
Most organizations prioritize cloud flexibility—and let application teams choose the best environment...

32 Security Experts on Changing Endpoint Security
For many companies, the modern business environment has become a mobile workplace in which employees...

Telstra's Best Practice Guide to Hybrid Cloud
Hybrid Cloud is becoming the strategy of choice for enterprises that want the best of both public cloud...

Veeam Enterprise Availability for SAP HANA
Enterprise-grade companies uses SAP HANA worldwide, this is the application directly related to customers...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.