IT Security

Why automation is essential for cyber resilience
Digital transformation makes today's businesses more productive and more vulnerable to cyberattacks....

Redefining Data Loss Prevention
Data doesn't move itself. People—whether they are negligent, compromised or malicious—move data in...

Get a Fast Office 365 User Experience
Recommendations for a smooth migration, fast results. A Microsoft Office 365 migration can be daunting....

Leadership trends report: operating excellence
Optimising business operations used to mean just lowering costs and increasing profits. But today, you...

7 Experts on Moving to a Cloud-based Endpoint Security Platform
Without a doubt, endpoint security has become an urgent priority for many organizations, and it's not...

Encryption Is Now a Trojan Horse: Ignore It at Your Peril
The game of leapfrog between hackers and data security professionals continues. No sooner do organizations...

How to Stop Ransomware Attacks
This ebook How to Stop Ransomware Attacks provides in-depth guidance for quickly setting up stronger...

Rebellions and rejections report
The global pandemic forced organizations to pivot rapidly from an office-based workforce model to one...

Forrester A Practical Guide To A Zero Trust Implementation
Secure Workload Access On Your Journey To Zero Trust Including the licensed Forrester report: A Practical...

Building the Business Case for Improving Endpoint Security
As a security provider, we understand that convincing executives to make changes to their stack can be...

Combatting Ransomware by Exposing the Myths
Ransomware continues to pose a credible and costly threat to the enterprise. Misinformation only compounds...
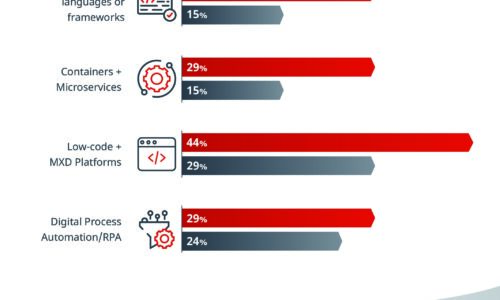
What Separates the Best from the Rest
Some IT organizations have the speed and adaptability to change course quickly when disaster strikes...

The State of Application Security in 2021
Barracuda commissioned independent market researcher Vanson Bourne to conduct a global survey of 750...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.
