IT Security

Moor Insights: Cloud is Built on Modern Infrastructure
The modern enterprise lives in a multi-cloud world, where delivery of infrastructure resources and IT...

Optimized Security for Multi-Cloud laaS Environments
No question: Multi-cloud adoption can benefit your business. New question: How can you secure multi-cloud...

Forrester : Managing Security Risk and Compliance
The explosion of data and proliferation of devices demands better security tools and monitoring from...

10 Benefits of Oracle’s Data Management Platform
Accelerating business change begins with the proper management of an organization's data. With Oracle's...

Blackberry Guard: Solution Brief
While cloud and mobile technologies provide significant opportunities for digital transformation, they...

Elastic Cloud Gateways: The Evolution of Secure Cloud Access
Enterprise security groups today face a daunting task. While their core responsibility of protecting...

Enterprise NoSQL For Dummies
NoSQL represents a fundamental change in the way people think about storing and accessing data, especially...

3 Ways to Make Cloud your Business eBook
The role of IT infrastructure and operations leaders has dramatically changed, and cloud evolution continues...

Optimizing Workload Placement in Your Hybrid Cloud
Many IT organizations are in the process of modernizing their infrastructure, as part of either a digital...
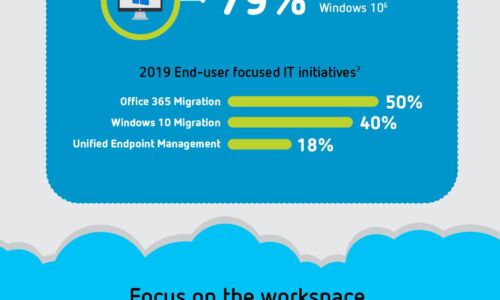
Digital Transformation: A Look Ahead
Digital transformation is reshaping organizations into digital businesses. Organizations are focused...

Securing Endpoints Amid New Threats
Giving employees the flexibility to be fully productive while working remotely makes it critical that...

An Insider’s Look at Enterprise Cloud Adoption
It's a well-known fact that more businesses are adopting cloud computing technologies, and the overall...

The Challenge of Migrating Higher Education Applications to the Cloud
Explore the challenges the higher education sector faces when it comes to migrating applications to the...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.
