IT Management

Secure Beyond Breach
Securing the perimeter is no longer enough. The focus has shifted to ensuring your organization continues...

Cloud Security Automation For Dummies®
Get the big picture on cloud security, in all its complexity, speed, and scale. Our Cloud Security Automation...

Identity: The Digital Trust Accelerator
As digital services play an increasingly amplified role in our lives, both who and how we trust is changing. Where...

5G for Dummies
5G, the next iteration of wireless networks, is not merely an incremental increase in network speed and...

Fleet Management and Compliance Mini Guide
When you increase compliance and reap great rewards in return, that's a win-win. Especially when the...
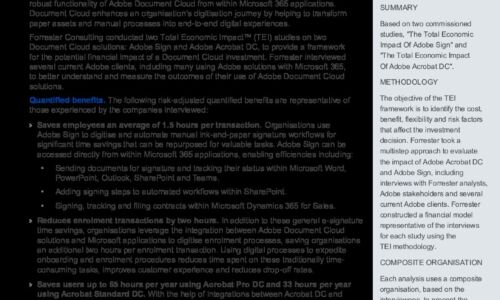
The Total Economic Impact of Adobe Document Cloud & Microsoft Spotlight
Forrester interviewed several current Adobe clients, including many using Adobe solutions with Microsoft...

Digital Controllers Optimize, Digital Transformers Innovate
This resource is published by Dell and Intel®. In December 2017, Dell commissioned Forrester Consulting...

The role of CIO in a world where experience rules
In recent years, the role of CIO has evolved to meet a wider set of responsibilities and aspirations....

Where you need trust, you need PKI
On a rainy summer day in 2013, a small, float-equipped plane stalled while flying low over the mountains...

The AI & Machine Learning Imperative
Companies across various industries are seeking to integrate AI & machine learning (ML) into workflows...

The 8 benefits of cloud and how you can achieve them for your business
Digital transformation is firmly upon us. In fact, Gartner predicts that 75% of businesses will transform...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


