
Security Starts Here: Privileged Access Management
The threat of a security incident or critical error is very real, and it's something that auditors are...

Financial Crime Convergence: Think Collaboration, Not Consolidation
Silos within financial crime functions are the criminal's best friend. Malicious actors have exploited,...

Functional Programming For Dummies
Using functional programming techniques can make you incredibly efficient when solving certain problems...
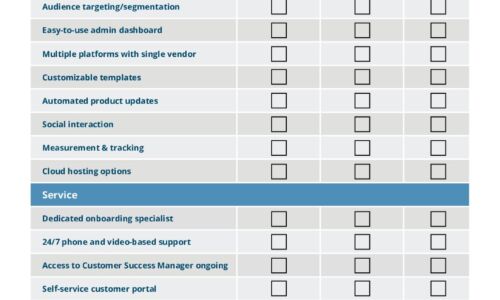
IT Comms Plan Bundle
IT teams need to communicate important messages across their organization – from scheduled maintenance...

Don't Diverge—Converge
Digital acceleration is driving the adoption of hybrid IT architectures. These new hybrid environments...

Mind-blowing customer experience starts here
Now is the time to take your digital transformation in a new, more effective direction. At ServiceNow,...

Artificial Intelligence: The Smarter Approach To Information Security
The news headlines are replete with stories of devastating data breaches, compromising the personal and...

Stay open for business — but closed to cyberthreats
E-commerce relies on always-on connectivity to customers whenever they want to access services. Your...

Responding Smarter, Faster and Better
In cybersecurity, a critical event is a major incident that's disruptive enough to pose a meaningful...

Building a Digital Infrastructure for the Entire Organization
Building a Digital Infrastructure for the Entire Organization Today's business world increasingly demands...

A Guide for SMBs: Can I really become “less hackable”?
After nearly 20 years working in cybersecurity, I am still asked the age-old question by business owners:...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


