
How to Make a More Efficient IT Helpdesk
There's a lot riding on today's Helpdesk Managers and their teams. As organizations have expanded in...

DDos is the New Spam: 3 Strategies to Turn Catastrophe into Annoyance
As DDoS attacks grow larger, more complex, and more pervasive, it can feel like we face a future of inevitable...

The Definitive Guide to SharePoint Migration Planning
Getting your SharePoint migration right is essential to a host of important goals, from business continuity...

How Malware Can Steal Your Data
As applications drive business, more and more valuable data is accessed and exchanged through them. Cybercriminals...
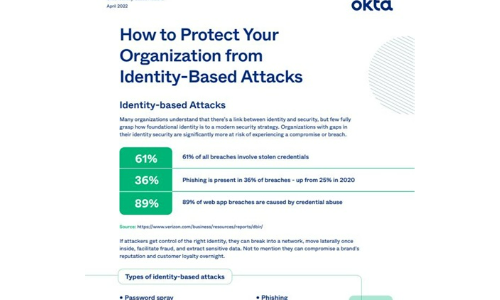
How to Protect Your Organisation from Identity-Based Attacks
Many organizations understand that there's a link between identity and security, but few fully grasp...

Functional Programming For Dummies
Using functional programming techniques can make you incredibly efficient when solving certain problems...

IDC MarketScape
Use the IDC MarketScape's U.S. Managed Detection and Response Services 2021 Assessment to learn more...

Proofpoint Security Awareness Training
Proofpoint Security Awareness Training Enterprise helps you deliver the right training to the right people...

Insider's Guide To Choosing a DNS Service
The need that DNS (the domain name system) was created to address seems simple enough: where can I find...

Navigating the new working paradigm
All of a sudden, remote working has become the norm. And we're coming to terms with the fact that this...

Automation antidotes for the top poisons in cybersecurity management
Cyberthreats are more imminent and dangerous than ever in terms of their persistence and severity. The...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


