Connectivity
Report: Forrester TEI for CSM
To deliver effortless, end-to-end customer experience every time, all parts of your organisation need...

The Book of Knowledge - HAandLC
Gartner predicts that 65% of all app development activity will take place on low-code platforms by 2024....

OWASP Top 10
The nonprofit Open Web Application Security Project (OWASP) works to improve the security of software,...

Key Steps to Optimizing Cloud Security
Do you know what's missing from your cloud security strategy? There's no question that moving to the...

The State of Electronic Signature
Today's organisations can't wait any longer to make the digital transformation. It's no longer simply...
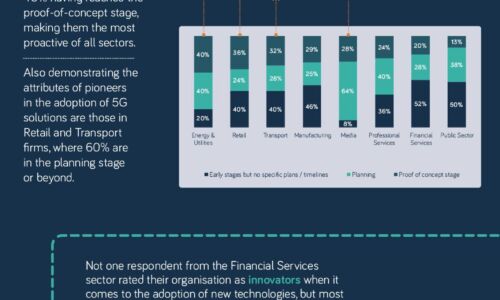
The 5G opportunity within UK industry
Neos Networks research shows that two thirds of organisations expect to have made significant investment...

The Threat That Never Goes Away
While digital acceleration and work-from-anywhere strategies may have been driven by the uncertain times...

VMware Cloud Workload Migration Tools
Before starting a cloud migration project, it is critical to understand the strategies and tools available...

Mobile Testing with Sauce Labs
Sauce Labs offers the broadest mobile testing solution in the industry to help modern mobile development...

Overcoming the Top Five Gaps in Office 365 Data Protection
Microsoft Office 365 is widely used. Whilst it does offer a variety of system availability and data protection...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



