Connectivity

Protecting Every Edge To Make Hackers’ Jobs Harder, Not Yours
Today's users need a network that allows them to connect to any resource from any location using any...
Don’t Diverge—Converge
Digital acceleration is driving the adoption of hybrid IT architectures. These new hybrid environments...

Aruba's Roadmap To Hybrid Workplace Success
After the initial network overhaul to enable work from home at the start of the pandemic, organizations...

10 Tech Trends for Retail: Navigating 2021 and Beyond
While last year was a difficult one for the industry, retailers are leaning in to new technologies to...

Digital Transformation & Risk for dummies
Digital transformation is a critical priority for many companies across most industries, and it's more...
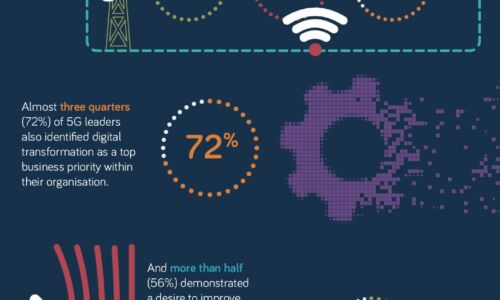
What makes a 5G Leader?
With 5G a still nascent technology, opportunity remains for businesses to accelerate adoption of this...

7 Common Ways Ransomware Can Infect Your Organization
Understanding how ransomware infects a device and spreads across a network is crucial to ensuring that...

Build your future, faster
To support the organization in its pursuit of innovation, and to address future uncertainties, development...

IT’s 5 Toughest Work from Home Challenges and How to Solve Them
2020 forced the shift to a hybrid work model Unexpectedly, you found yourself working from home. The...

MITRE Engenuity™ ATTandCK® Evaluation
MITRE has become the common language of EDR and is the de facto way to evaluate a product's ability to...

Navigating the new working paradigm
All of a sudden, remote working has become the norm. And we're coming to terms with the fact that this...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


