Analytics

Industrial Engineering Leader Aims to Protect Data
Fives is an industrial engineering group, headquartered in Paris, France. It designs and manufactures...

Fortinet Secures the Intelligent Enterprise Running SAP
Business leaders embrace SAP HANA functionality to stay on top of emerging trends and evolving business...

Traditional Pentesting: A Turtle Chasing A Cheetah
Why Pentesting Needs to Evolve. Antiquated legacy penetration testing methods fail to catch all the critical...

Splunk Predictions 2020
The future is data. In a rapidly digitizing world, data is at the root of every opportunity, and essential...

How Proofpoint Defends Against Ransomware
Stop ransomware from taking root and spreading in your organisation. Ransomware attacks are becoming...

Unlock the Power of Hybrid Cloud with Consistent Operations eBook
Embracing a hybrid cloud operating model creates new possibilities for IT organizations, paving the way...
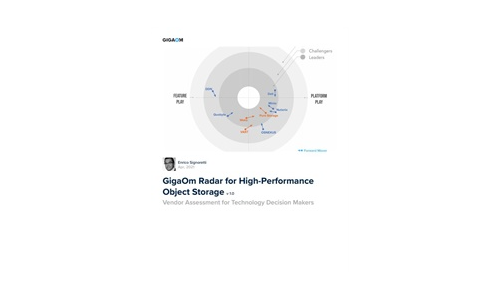
GigaOm Radar for High-Performance Object Storage
For quite some time, users have been asking for object storage solutions with better performance characteristics....

How 5 Enterprises Consolidated ITSM to Reduce Costs
See how five leading brands modernized ITSM with ServiceNow. For businesses that want to transform, modernizing...

Bringing Everything Together in Automotive
Today's Automotive Industry is Certainly Not Short of Data, it's coming from everywhere. From wind tunnels,...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.




